How To Install Snort Ids On Ubuntu Iso
Below is our Snort and Snort Report Installation Guide for the current versions as of this writing – Snort 2.9.7.2 and Snort Report 1.3.4. This guide is also available. This document will enable you to set up a full intrusion detection and prevention system (IDS/IPS) using free software. Introduction The purpose of this document is to provide the user with a simple installation guide to get Symmetrix Technologies’ Snort Report up and running with Sourcefire’s Snort intrusion prevention and detection system on Ubuntu Linux. Please note that package numbers change often but were current as of this writing. Equipment Assumptions A dedicated PC for the Snort IDS/IPS (the faster the better) with two network cards An additional PC for IDS/IPS administration A broadband Internet connection A method to burn ISO files to a blank CD Knowledge Assumptions A working knowledge of Linux including SSH and editing configuration files with vi A basic knowledge of TCP/IP and network topologies Use of the Backslash There are many instances in this document where a command will not fit on one line so the commonly accepted backslash is used to split it into multiple lines.

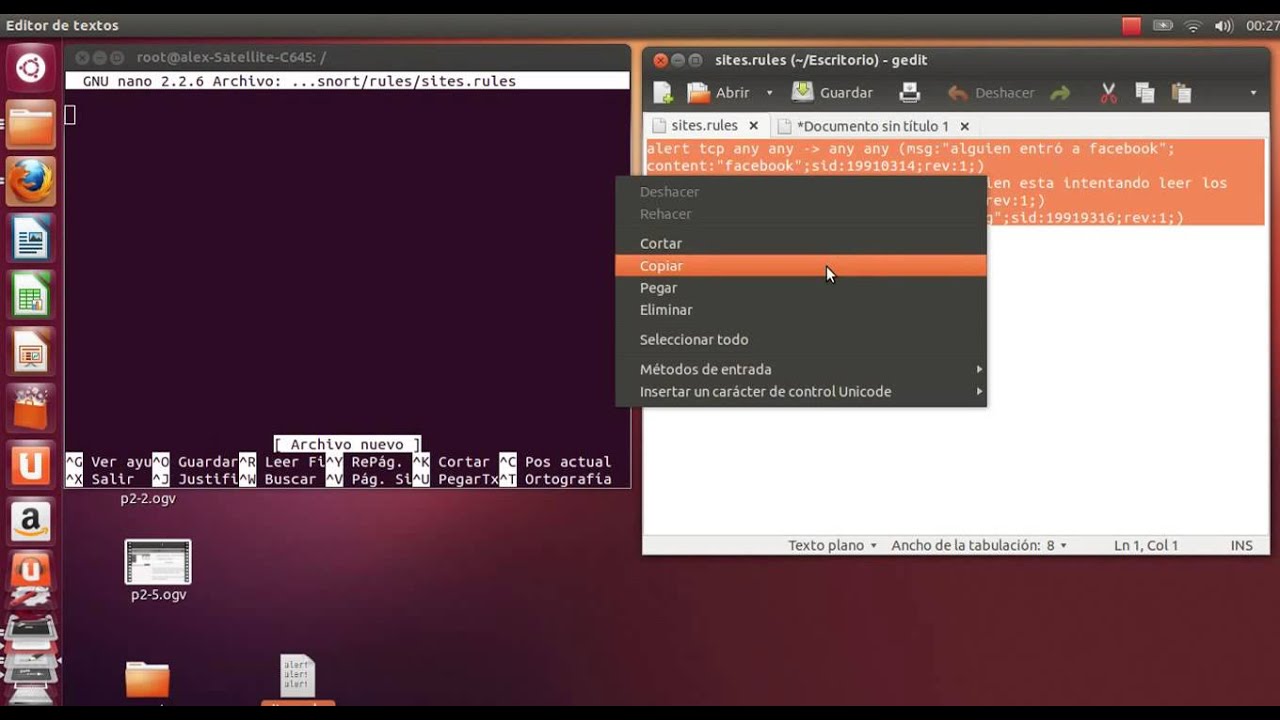
Installing Snort 2.9.7.x on Ubuntu. Of installing and configuring Snort as a Network Intrusion Detection System. For installing Snort install this. To run Snort on Ubuntu safely without root access, you should create a new unprivileged user and a new user group for the daemon to run under. Sudo groupadd snort sudo useradd snort -r -s /sbin/nologin -c SNORT_IDS -g snort. Then create the folder structure to house the Snort configuration, just copy over the commands below.
For example, this is one command, not two: /usr/local/snort/bin/snort -D -u snort -g snort -c /usr/local/snort/etc/snort. Torrent American Gangster Ita. conf -i eth1 If you are copying and pasting you can leave the backslashes in place and Linux will understand it. End Result There are many ways to set up Snort – we’re going with a pretty simple deployment. The end result will be a dedicated IDS machine that actually does the sniffing and a workstation where you perform administration and view the attacks detected by Snort. The following diagram illustrates the topology.